Technology
Israeli firm Check Point informs about the appearance of a new kind of Trojan Simplocker, infecting mobile devices with OS Android. In it we use other methods to stimulate the installation of more aggressive means of blackmail and non-trivial link with the managed server.
The updated version of the Trojan encrypts files, removes the originals and locks the screen, displaying a message overlay ransom. In the text on behalf of the NSA and the US Treasury Department is required to translate a “fine” of $ 500 through PayPal to the specified account, otherwise the amount of debt will increase every day. Specifies various pretexts, and copies the text style formal notice.

Trojan not only imitates messages from government agencies, but also disguised as popular programs – in particular, the application stores and Flash Player. Gives his request administrative rights, which is the utility without system functions never do.
According to the head of the research group Check Point Ofer Kaspi, Trojan difficult to remove once it gains control of the device. Encrypted files can not practically be recovered without the key, so the victim has two options: pay for the transcript of the required amount (usually $ 500) or to reset to factory settings, losing all personal data.
About the need make backups, cloud synchronization and basic safety rules, you can write almost every day. Mass infection still becomes possible due to the fact that the level of competence of users has been steadily falling. Simplocker did not contain any means to circumvent the protection of Android. He only asks for the necessary privileges from the user. Despite the obvious trick, many victims are allowed to own and malicious activity unknown applications.
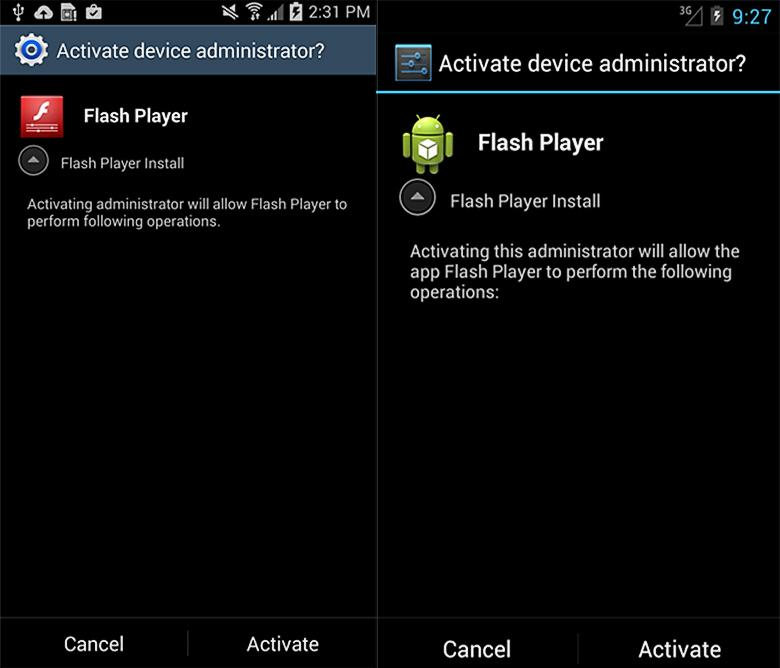
Troyan Simplocker masquerades as a Flash Player (Image: Check Point / Avast! ).
According to Check Point number of infected tens of thousands of devices. It continues to rise even after the targeted fight against trojan, release free antivirus utilities and advocacy. Some even paid several times to get your files back. They are either re-infected, or simply do not consider it necessary to take action, even after have faced blatant blackmail.
Most of the Trojans extortionists does not store the key locally and get it from one of the managed server. This makes it difficult to restore files, because each time the key is different, and there is no place to take him. Therefore, faced with the beginning of the epidemic, anti-virus companies often use the method to identify the sinkhole and blocking botnet control servers. Without them, the Trojan loses the ability to encrypt files with a unique key and its main malicious features.
Most of the Trojans communicate with the C & amp; C server over HTTP or HTTPS. Such traffic is quite specific, so it is relatively easy to track. There are a number of waste procedures to identify and eliminate such botnets, with the assistance providers.

traffic analysis using sniffer Wireshark (screenshot: threatpost.com).
The new version Simplocker connection with the C & amp; C servers installed protocol instant messaging XMPP (formerly known as Jabber), so the traffic Trojans lost on the general background. Using XMPP also makes it impossible to lock certain nodes from a URL.
There are other reasons to use XML-based protocol for the management of malware. Because it used a third-party and already present on the Android library, the Trojan turns a little and do not require additional components. Because XMPP supports TLS, the connection between the infected device and command server is encrypted by standard means.
For more difficulty blocking the botnet is to use it in the network nodes TOR. In addition to encryption keys Trojan receives the same way and the team. Among them may be the task of sending an SMS or make calls to premium rate numbers, search and send passwords, sending spam, delete user files on your device and the other.

Analysis of Trojan Simplocker (screenshot: Check Point).
Get a few samples of the new version of the Trojan, the researchers Check Point still managed to intercept the hundreds of thousands of messages sent between servers on the XMPP C & amp; C and infected mobile devices. All the information they contain garbage, introduces the purpose of the analysis packages difficulties. Overcoming obfuscation techniques, they were able to read the contents of all messages.
The analysis showed that the requested amount changes extortionists. It ranges from $ 200 to $ 500, and about 10% of the victims in a hurry to make a payment in the first hours. Authors Simplocker have received at least half a million dollars, and it is certainly only the tip of the iceberg. Experts Check Point received only some of the control messages. The real extent of the infection in their opinion many times more.
It was noted that after the successful infection of the Trojan determines device location by GPS or network operator. Knowing where the victim, the Trojan displays adapted for residents of the region report. Localization performed quite well, underscoring the high level of the criminal group. About two-thirds of infected gadgets found in the United States. The second highest number of infections is Asia, Europe and closes the list. In Russia, too, there have been cases of infection, but complete confidence in the fact that we are talking about the new version Simplocker yet.

The automatic language selection for the screen lock Trojans Simplocker (screenshot: Check Point).
Currently, employees Check Point and other anti-virus companies try to identify and isolate the C & amp; C botnet servers. XMPP-server operators notified and thousands used to control the trojan already blocked accounts. However, the Trojan also not lose time and come up with workarounds.
See also
No comments:
Post a Comment